Multi-Factor Authentication (MFA) FAQs
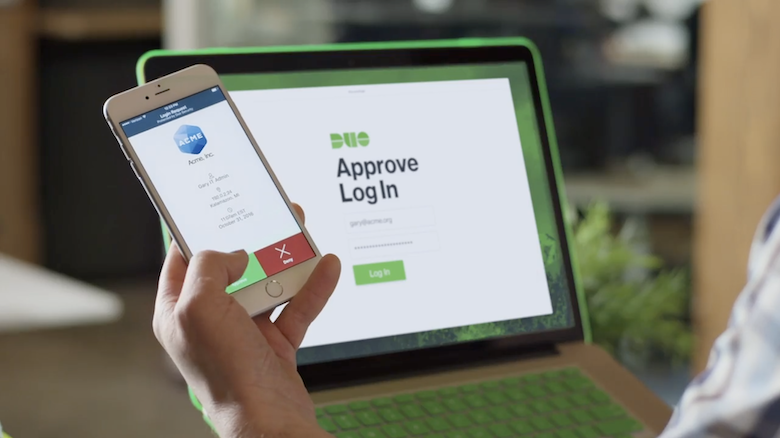
Multi-factor authentication (MFA) is highly effective yet often misunderstood tool to fend off account compromise attacks. Here are the answers to some frequently asked questions about MFA.
Multi-factor authentication (MFA) is one of the best tools companies can use to fend off cybercriminals trying to compromise business accounts. It blocks 99.9% of account compromise attacks. It also helps thwart automated bot, phishing, and targeted attacks.
Although MFA is very effective at protecting online accounts, many companies do not take advantage of it. This is partially due to not having enough time to research the subject to get their questions answered. To jumpstart their learning curve, here are the answers to some frequently asked questions about MFA.

What is MFA?
MFA, or multi-factor authentication, is a layered approach to securing data and apps, according to the Cybersecurity and Infrastructure Security Agency (CISA). Users must provide two or more credentials to verify their identity when logging in to a system. That way, even if hackers have compromised one of the credentials, they won’t be able to access the system because they won’t have the remaining credential(s).
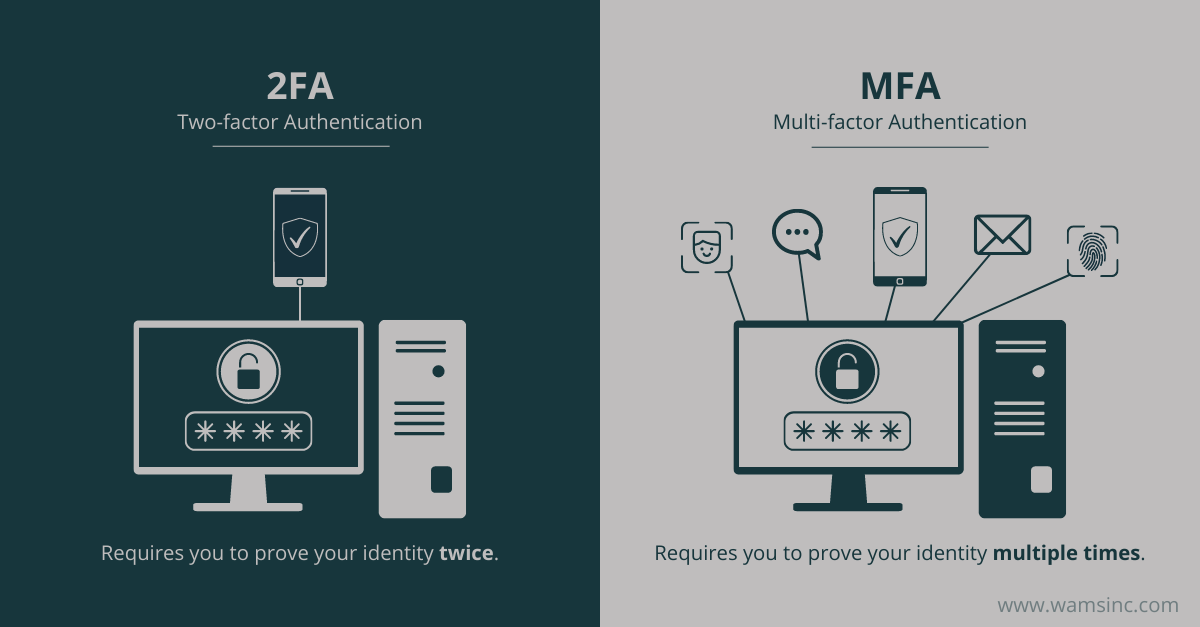
Is Two-factor Authentication the Same Thing as Multi-factor Authentication?
Two-factor authentication is a form of multi-factor authentication. When users must provide two credentials to verify their identity when logging in to a system, it is referred to as two-factor authentication. When users need to provide three credentials, it is called three-factor authentication.
What Kinds of Credentials Can Be Used?
Many different types of credentials are used in MFA. They fall into three categories:
- Something you know: Examples of credentials in this category include passwords, personal identification numbers (PINs), and one-time passcodes.
- Something you have: This group contains physical devices that are used for verification, such as security keys, cryptographic tokens, and smartphones with an authenticator app.
- Something you are: Faces, fingerprints, irises, and several other parts of the human body are unique to an individual, so scans of them can be used for verification.
When designing an MFA system, you can choose to use credentials from the same category or different ones. For example, you can design a system that uses passwords and one-time passcodes or a system that uses security keys and facial recognition.
Companies commonly use two-factor authentication in which the first required credential is a password and the second one is a passcode that’s sent via a text message, email, or phone call. Push notifications from authenticator apps are also frequently used with passwords.
Can MFA Be Bypassed?
When it comes to MFA bypass attacks, it’s a “good news, bad news” situation. Let’s look at the bad news first. Virtually all of the authentication methods used in MFA are vulnerable to bypass attacks, according to Microsoft. For example, push notifications from authenticator apps and one-time passcodes sent via text message, email, or phone call are vulnerable to channel jacking and real-time phishing attacks.
Now for the good news. Attacks that target MFA are rare because MFA is costly to hack, no matter what authentication methods are being used. “Use of anything beyond the password significantly increases the costs for attackers, which is why the rate of compromise of accounts using any type of MFA is less than 0.1% of the general population,” said Microsoft. “MFA is the least you can do if you are at all serious about protecting your accounts.”
If you have any more questions about MFA or would like more information about it, get in contact with our team of experts, please email info@wamsinc.com or call (800) 421-7151. With WAMS, we will be responsible for your small to medium sized firm or business with our IT solutions and managed services.
